Greetings readers! In this article I'll demonstrate how to use Nmap for traceroute and DNS lookups. The Nmap suite not only allows you to perform network scans, but also provides various useful features like ping, traceroute, reverse DNS lookups etc.
Traceroute with Nmap
The traceroute in Nmap is similar to the traceroute or tracepath command found in various linux/unix distributions. A simple traceroute can be performed using :
nmap --traceroute 10.0.2.4
Force Reverse DNS Resolution
If no options are specified, Nmap will look for reverse DNS for hosts which are either alive or appear to be alive. Force DNS is useful when looking for blocks of IP addresses as Nmap will resolve the reverse DNS of every IP address. A force reverse DNS resolution can be done using :
nmap -R 10.0.2.4
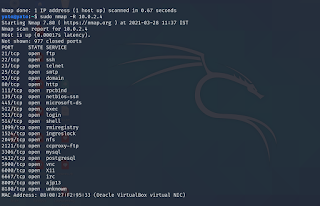
Nmap force reverse DNS resolution

Alternative DNS Lookup Method
The --system-dns option instructs Nmap to use the host system’s DNS resolver
instead of its own internal method.
nmap --system-dns 10.0.2.4
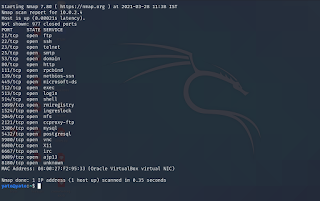 |
| Nmap system DNS lookup |
Disable Reverse DNS Resolution
Specifying reverse DNS resolution can take a significant amount of time, which becomes inconvenient while scanning a large number of hosts. Disabling reverse DNS lookups can save a lot time in such scenarios. It can be disabled using :
nmap -n 10.0.2.4
Manually Specify DNS Servers
We can specify or configure manual DNS servers for nmap search query. Manual DNS servers can be specified using :
nmap --dns-servers 208.67.222.222,208.67.220.220 10.0.2.4
Creating A Host List
We can create a list of DNS names for the specified systems. This method becomes useful for identifying the IP addresses and DNS names for the specified
targets without sending any packets to them. This can be done using :
nmap -sL 10.0.2.4/24





